26+ Free Application Security Checklist Templates – PDF, Word
In an automated world where technology prevails, it has become increasingly important to safeguard our personal and professional data from external threats. Consequently, application security has emerged as a critical aspect of the software development process. To ensure that such applications are secure and efficient, experts in the field have compiled a checklist template that highlights all the necessary elements that an application should possess.
Table of Contents
This template acts as a guide as it helps developers, testers, and auditors create secure, reliable software. With this checklist as a base, one can rest assured that the software they produce adheres to the highest levels of security standards and protects both themselves and their users from any potential security breaches.
Download Free Application Security Checklist Templates
Benefits of Implementing an Application Security Checklist
Implementing an application security checklist is not only a necessary step for protecting sensitive data, but it also offers several benefits for businesses. Firstly, having a security checklist in place can help identify potential weaknesses and flaws in application code, ultimately reducing the risk of breaches and cyber-attacks. Secondly, it promotes a culture of security within the organization, encouraging employees to prioritize security in their daily tasks.
Thirdly, a security checklist allows for consistent and repeatable security measures, ensuring that no important steps are missed during the development process. By implementing an application security checklist, businesses can not only safeguard their sensitive data but also build trust and confidence with their customers.
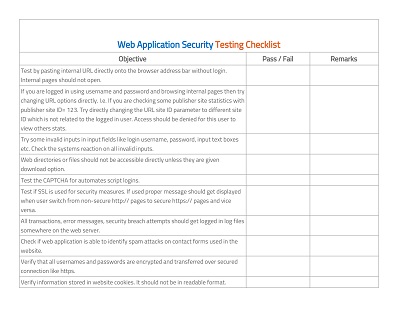
Understanding Application Security Threats and Risks
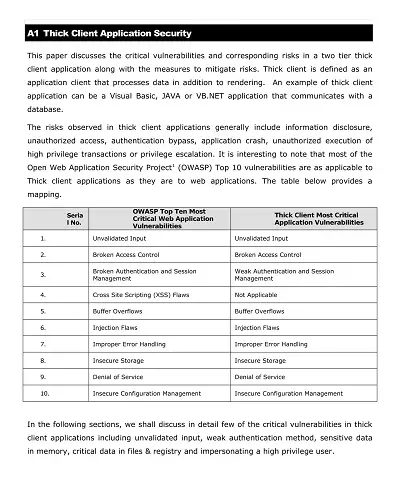
As our world has become increasingly reliant on technology and software, understanding the risks associated with application security has become essential. This encompasses a wide range of potential threats, including malware, phishing attacks, and unauthorized access to sensitive data.
The consequences of these risks can be costly, with potential damage to a company’s reputation, financial stability, and even legal issues. Therefore, individuals and organizations must be proactive in identifying potential security threats and implementing measures to prevent them. By prioritizing application security, we can mitigate risks and ensure the confidentiality, integrity, and availability of our information.
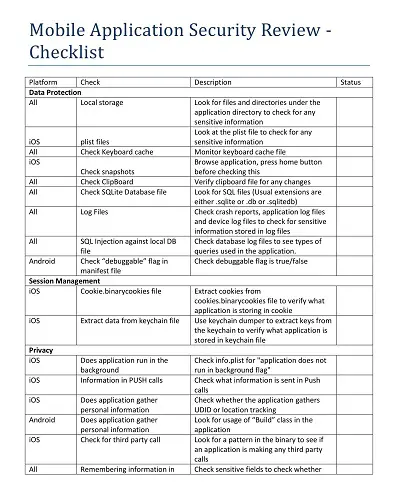
Key Components of an Application Security Checklist
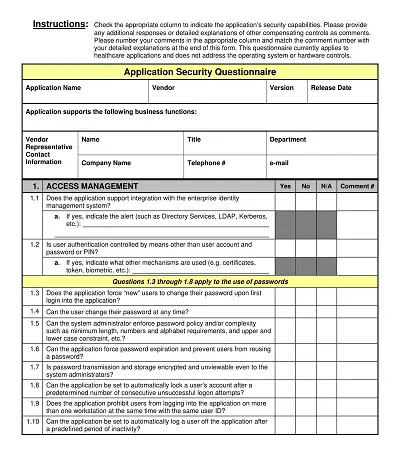
When it comes to application security, there are a few key components that every checklist should include. First and foremost is authentication and access control. This means ensuring users are who they say they are and only have access to the features and data they are authorized to. Another critical component is encryption, which protects sensitive data both in transit and at rest.
Regular vulnerability scans and penetration testing can help identify potential weaknesses in the system and allow for proactive measures to be taken. Finally, it’s important to have a plan for incident response and disaster recovery in the event of a breach or other security incident. By including these components in an application security checklist, businesses can better protect themselves and their users from potential threats.
Establishing Application Security Standards and Policies
In today’s technology-driven world, applications are at the core of businesses, from small start-ups to large enterprises. While increasing technological advances present numerous benefits, they also pose a significant risk to an organization’s security. Establishing strong application security standards and policies is essential to protect your business from cyber-attacks, data breaches, and unauthorized access.
It is a proactive approach that involves assessing and identifying potential vulnerabilities, mitigating risks, and ensuring compliance with security regulations and best practices. Effective application security standards and policies include incorporating multiple layers of security controls, regular vulnerability scanning, and continuous security testing to ensure the highest level of protection for your organization’s data and applications.
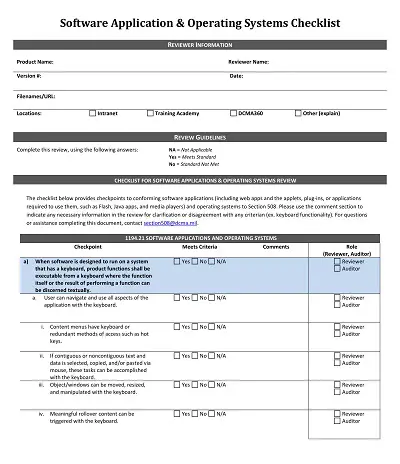
How to Create an Application Security Checklist Template
In today’s digital world, cyber threats are constantly increasing and posing a significant risk to businesses and organizations. As a result, application security has become a critical issue that cannot be ignored. An application security checklist template is a helpful tool that helps businesses to identify, assess, and mitigate weaknesses in their applications.
Identify the Key Components of the Checklist
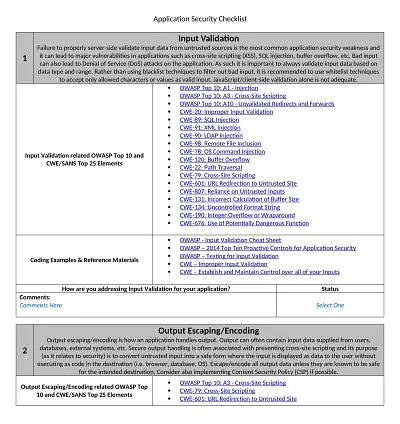
Before creating an application security checklist template, one should identify the key components that should be included in the checklist. Some of the key components include authentication, access control, input validation, encryption, error handling, and data backup. These components are crucial for the security of an application, and they should be included in the checklist.
Determine the Assessment Methodology
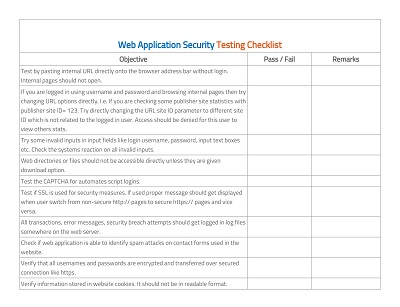
An effective application security checklist template should include an assessment methodology that helps to identify and assess the vulnerabilities in an application. One can use different assessment methodologies such as manual assessment, automated assessment, or a combination of both. Each assessment methodology has its advantages and disadvantages, and one should choose the most suitable one for their business.
Develop a Scoring System
A scoring system is essential in an application security checklist template as it helps in prioritizing vulnerabilities. The scoring system should be based on the level of risk posed by the vulnerability, the ease of exploitation, and the potential impact of the vulnerability. By assigning a score to each vulnerability, businesses can prioritize the vulnerabilities that need immediate attention.
Establish a Remediation Plan
A remediation plan is a critical component of an application security checklist template. It helps in creating a roadmap for mitigating vulnerabilities in an application. The remediation plan should include the steps to be taken to fix vulnerabilities, the timeline for implementing the fixes, and the responsible parties.
Regularly Update the Checklist
The threat landscape is constantly changing, and vulnerabilities that were not present a few months ago may be present today. Therefore, it is essential to regularly update the application security checklist template. The checklist should be updated to include new threats, vulnerabilities, and assessment methodologies. Updating the checklist ensures that businesses are up to date on the latest threats and vulnerabilities.